Collective defense brings entities together against common threats—exemplified by NATO's formation to counter Soviet expansion. In cybersecurity, organizations share threat intelligence and collaborate despite market competition. IT Agent (formerly TrackD) extends this principle to patch management, providing crowdsourced deployment data that transforms cautious, fear-based patching into confident, data-driven vulnerability remediation.
Read time: 4 minutes
The Double-Edged Sword of Configuration
Every IT operation relies on some form of endpoint management solution to deploy software and patches. Whether it's Microsoft Intune, remote management and monitoring (RMM) products like Atera, Datto, ConnectWise, NinjaOne, or Kaseya, or the Windows Update Agent (WUA) itself, these tools share a common characteristic: extensive configurability.
This flexibility represents both the greatest strength and most significant weakness of endpoint management platforms. The same configuration options that allow organizations to tailor deployments to their specific needs can inadvertently sabotage their security posture.
Understanding Windows Update Agent Mechanics
WUA exemplifies this configuration complexity. As an integral component of the Windows operating system, WUA handles the entire update lifecycle: checking for Windows updates, retrieving them from Microsoft Update or Windows Server Update Services (WSUS), and installing them on endpoints.
WUA's configuration options span from fully automated installation to manual user prompts. While this flexibility accommodates diverse organizational needs, it also creates opportunities for misconfigurations that compromise security effectiveness.
The Deferral Window Trap
Organizations frequently configure endpoint management tools to postpone patch installation based on a flawed risk calculation. The logic seems reasonable: delay patch deployment so that disruptive updates break other networks first, allowing vendors to identify and fix problematic patches before they affect your systems.
This approach assumes that patches causing disruption will be quickly identified and resolved, while non-disruptive patches can be safely installed after the deferral period. Organizations accept the risk of running unpatched systems during this window, betting that cyber compromise is less likely than patch-induced disruption.
This risk assessment encapsulates the governing philosophy of vulnerability remediation for the past three decades: the fear of disruption outweighs the fear of cyber breach.
The Real-World Impact
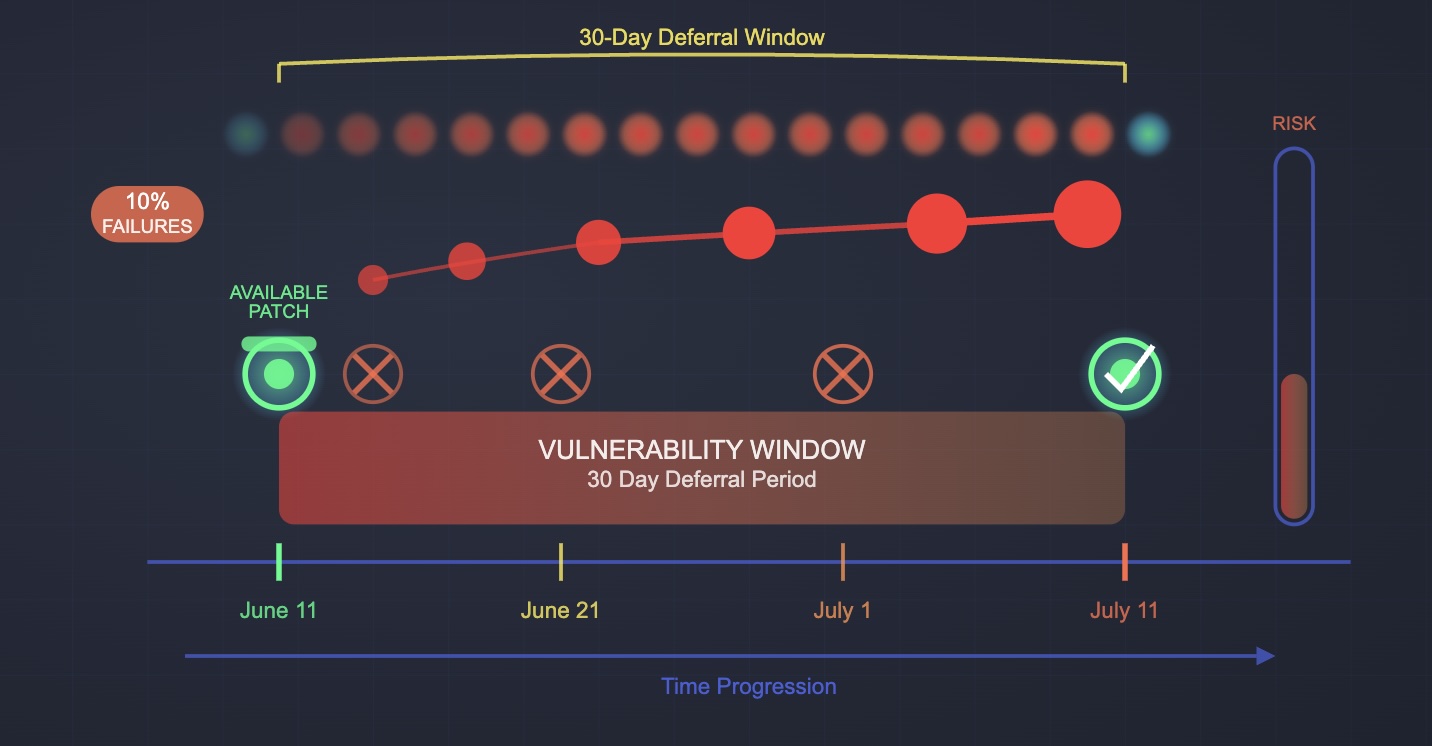
At IT Agent, we observe the practical consequences of this mindset regularly. Deferral windows account for approximately 10% of patch failures in managed environments—a significant percentage representing thousands of vulnerable systems remaining unprotected unnecessarily.
The mechanics are straightforward but the implications are serious. Consider a patch released on Patch Tuesday, June 11th. If an organization has configured a 30-day deferral window, any patching solution attempting to install that update on June 11th will fail because the endpoint management system blocks installation until July 11th.
This month-long exposure window creates precisely the security gap that modern threat actors exploit most effectively.
The Psychology Behind the Practice
The psychological foundation of deferral windows reflects a rational but increasingly outdated fear. IT practitioners have endured patch-induced service disruptions that created hours or days of troubleshooting, user complaints, and potential career consequences. These experiences naturally foster cautious approaches to patch deployment.
However, this caution is rooted in historical experiences that no longer reflect current realities. Contemporary patches cause disruption in less than 2% of deployments, yet many organizations operate as if every patch poses significant risk until proven otherwise.
The Anachronistic Risk Model
The traditional deferral approach made sense when patches frequently caused problems and threat actors were less sophisticated and numerous. Today's environment has inverted this risk equation completely.
Modern cybercriminals operate with industrial efficiency, often exploiting known vulnerabilities within hours or days of disclosure. The window between vulnerability publication and active exploitation continues to shrink, while organizations maintain month-long deferral policies designed for a different era.
Meanwhile, modern software development practices, automated testing, and staged deployment methodologies have dramatically improved patch quality and reliability. The elaborate defensive measures once necessary to protect against frequent patch failures now primarily serve to delay essential security updates.
Beyond Traditional Approaches
The fundamental challenge with deferral windows lies in their blanket approach to risk management. These configurations treat all patches as equally risky, delaying both critical security updates and routine maintenance patches without distinction.
Effective patch management requires intelligence-driven approaches that can differentiate between patches likely to cause issues and those that can be safely deployed immediately. This distinction demands more sophisticated analysis than simple time-based deferrals can provide.
The IT Agent Solution
IT Agent's vulnerability management platform addresses this challenge by providing real-world intelligence about patch behavior across diverse network environments. Rather than relying on arbitrary time delays, our platform delivers insights about how specific patches have performed on similar systems before deployment.
This intelligence enables IT teams to patch aggressively when data supports immediate deployment while taking additional precautions only when evidence suggests potential issues. The result is dramatically reduced exposure windows without increased disruption risk.
Moving Past Fear-Based Configurations
The prevalence of deferral windows reflects broader challenges in cybersecurity decision-making. Fear-driven policies often create the problems they're designed to prevent, while evidence-based approaches enable both security and operational effectiveness.
Organizations need the confidence to abandon configurations that no longer serve their interests. This transformation requires more than policy changes—it demands access to intelligence that supports informed risk decisions.
The Path Forward
Deferral windows represent a legacy approach to patch management that prioritizes avoiding disruption over preventing compromise. In today's threat environment, this priority order creates unacceptable security gaps.
The solution isn't to eliminate all caution from patch management, but rather to replace blanket delays with intelligent, risk-based decisions. When organizations have confidence in their patch deployment decisions, deferral windows become unnecessary artifacts of a more cautious era.
Closing the Window
Every day that patches remain deferred represents another opportunity for threat actors to exploit known vulnerabilities. While organizations wait for others to test patches that statistically won't cause problems, attackers actively scan for and exploit the very vulnerabilities those patches address.
The question facing IT teams isn't whether to eliminate deferral windows, but whether they can afford to maintain them. In an environment where cyber threats evolve daily, month-long security gaps represent unacceptable risk.
Powerful, self-serve product and growth analytics to help you convert, engage.


