Collective defense brings entities together against common threats—exemplified by NATO's formation to counter Soviet expansion. In cybersecurity, organizations share threat intelligence and collaborate despite market competition. IT Agent (formerly TrackD) extends this principle to patch management, providing crowdsourced deployment data that transforms cautious, fear-based patching into confident, data-driven vulnerability remediation.
Read time: 4 minutes
The Industry's Misplaced Focus
Since vulnerability management emerged as a cybersecurity cornerstone, the industry has developed sophisticated solutions for every imaginable challenge—except the fundamental one that created the discipline in the first place. Today's market offers:
Advanced Vulnerability Scanners that identify security flaws across complex infrastructures with impressive speed and accuracy
Intelligent Prioritization Engines that apply sophisticated risk scoring to help teams focus on the most critical vulnerabilities
Comprehensive Patch Management Platforms that automate deployment across diverse operating systems and applications
AI-Powered Analytics that promise to revolutionize how organizations understand and respond to security risks
These solutions address important technical challenges, but they're all building around the edges of the real problem. They answer every question security professionals might ask except the only one that truly matters: "Will this patch cause operational disruption?"
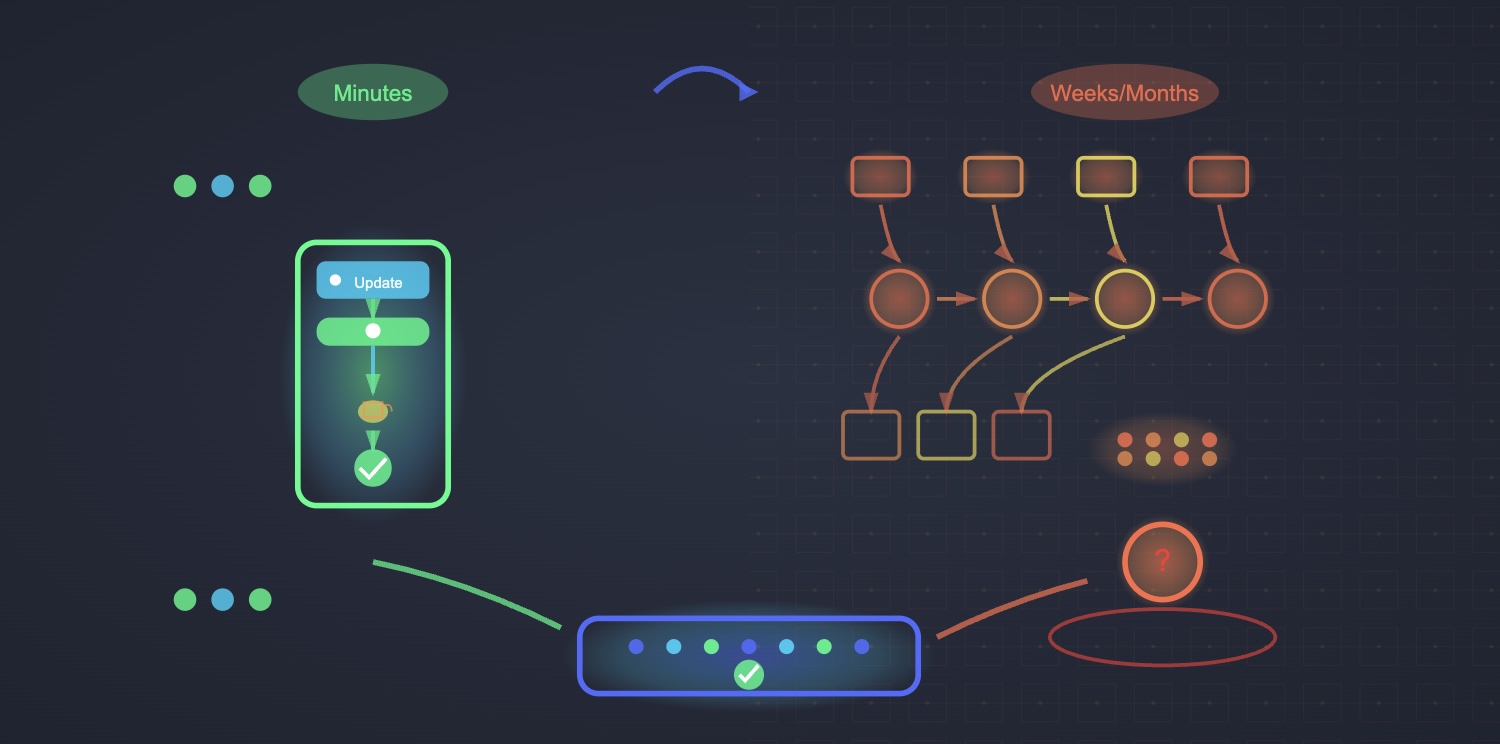
The Fear That Drives Complexity
Enterprise patch hesitancy stems from legitimate operational concerns. Unlike personal devices where disruption means individual inconvenience, enterprise systems support critical business processes where outages translate to revenue loss, productivity reduction, and potentially severe business consequences.
This fear has created elaborate workflows designed to minimize deployment risk through extensive testing, staged rollouts, and comprehensive change management processes. While these approaches provide some protection against patch-induced problems, they also introduce substantial delays that leave organizations vulnerable to active threats.
The irony is striking: in attempting to avoid operational risk, organizations create security risk. Extended patch cycles provide threat actors with larger windows to exploit known vulnerabilities, often turning theoretical risks into actual breaches.
The Missing Intelligence Layer
Traditional vulnerability management approaches this challenge backwards. They focus on identifying and cataloging vulnerabilities, then attempt to manage deployment risk through process controls rather than intelligence about patch behavior itself.
What's needed is direct insight into how patches actually behave in real-world environments. Instead of elaborate testing protocols based on limited internal scenarios, organizations need access to collective intelligence about patch reliability across diverse deployments.
This represents a fundamental shift from process-based risk management to intelligence-driven confidence. When teams know how patches have performed across thousands of similar environments, they can make informed deployment decisions rather than defaulting to cautious delays.
IT Agent's Revolutionary Approach
At IT Agent, we've built our platform around answering the question that matters most: "Will this patch cause problems in my environment?" Our approach represents a complete departure from traditional vulnerability management thinking.
While our platform includes comprehensive vulnerability identification and automated patch deployment capabilities, our differentiating capability lies in providing real-world intelligence about patch behavior. We collect data from thousands of deployments across diverse environments to understand how patches actually perform beyond vendor testing scenarios.
This intelligence enables organizations to patch with confidence when data supports immediate deployment while taking additional precautions only when evidence suggests potential issues. The result is dramatically faster patch cycles without increased operational risk.
Beyond Traditional Boundaries
Our vision extends beyond improving existing vulnerability management processes to fundamentally transforming how organizations think about security updates. We're working toward making enterprise patching as reliable and straightforward as personal device updates.
This transformation requires more than better tools—it demands new approaches that eliminate the artificial complexity that has accumulated around what should be a simple process. When organizations have confidence in patch reliability, vulnerability management becomes security maintenance rather than risk management.
The Technical Foundation
Achieving this vision requires sophisticated technical capabilities that go far beyond traditional vulnerability scanning or patch deployment:
Real-Time Vulnerability Discovery that identifies security flaws as they're disclosed rather than through periodic scanning cycles
Behavioral Intelligence Collection that understands how patches actually perform across diverse enterprise environments
Predictive Risk Assessment that can accurately forecast patch behavior based on environmental characteristics and historical deployment data
Automated Deployment Orchestration that applies patches with appropriate confidence levels while maintaining operational stability
These capabilities work together to create a fundamentally different experience where patch deployment becomes as routine and reliable as any other automated system maintenance.
Industry Transformation
The vulnerability management industry has invested decades in building increasingly sophisticated solutions around the wrong problem. Scanner accuracy, prioritization algorithms, and deployment automation all provide value, but they don't address the core concern that drives organizational hesitancy.
True innovation in this space requires confronting the fundamental question directly rather than building elaborate workarounds. When organizations can confidently answer "Will this patch break my systems?" with data-driven certainty, the entire vulnerability management paradigm shifts.
The Path Forward
Moving beyond traditional vulnerability management requires embracing intelligence-driven approaches that provide direct insight into patch reliability. Organizations need platforms that understand patch behavior across real-world deployments rather than just theoretical risk assessments.
This transition also demands cultural shifts where security teams focus on enabling rapid, confident deployment rather than managing elaborate risk mitigation processes. When patch deployment becomes predictably reliable, security improves while operational overhead decreases.
Eliminating Unnecessary Complexity
The ultimate goal isn't building better vulnerability management solutions—it's making vulnerability management unnecessary through reliable, automated security maintenance. Personal devices demonstrate that this vision is achievable when underlying processes are sufficiently reliable.
Enterprise environments can achieve similar simplicity when they have access to the intelligence needed to patch confidently. This requires platforms that understand patch behavior comprehensively rather than leaving organizations to guess about deployment risks.
The Future of Security Updates
IT Agent is building toward a future where enterprise security updates work as seamlessly as personal device updates. This vision requires solving the intelligence gap that has forced organizations to choose between security urgency and operational stability.
When enterprises can patch with the same confidence they have in personal device updates, vulnerability management transforms from a complex discipline into routine maintenance. This transformation will ultimately make organizations more secure while dramatically reducing operational overhead.
The question isn't whether this future is possible—personal computing has already proven the model works. The question is how quickly enterprises can adopt intelligence-driven approaches that enable the same reliability and simplicity in business environments.
Until the industry addresses the fundamental concern that drives enterprise patch hesitancy, vulnerability management will remain an artificially complex discipline that serves neither security nor operational objectives optimally. The solution lies in directly answering the question that actually matters rather than building increasingly sophisticated workarounds to avoid asking it.
Powerful, self-serve product and growth analytics to help you convert, engage.


