Collective defense brings entities together against common threats—exemplified by NATO's formation to counter Soviet expansion. In cybersecurity, organizations share threat intelligence and collaborate despite market competition. IT Agent (formerly TrackD) extends this principle to patch management, providing crowdsourced deployment data that transforms cautious, fear-based patching into confident, data-driven vulnerability remediation.
Read time: 7 minutes
Understanding the Vulnerability Landscape
Defining Modern Vulnerabilities
Vulnerabilities represent exploitable weaknesses in software, hardware, or network systems that threat actors can leverage to gain unauthorized access, steal data, or compromise system integrity. In contemporary IT environments, these weaknesses span an increasingly complex ecosystem of interconnected systems, applications, and infrastructure components.
Modern vulnerabilities exist across multiple layers: operating systems, applications, firmware, network devices, and even cloud configurations. Understanding this multi-layered exposure is essential for developing comprehensive patching strategies that address risks systematically rather than reactively.
Critical Vulnerability Categories
Today's threat landscape encompasses several categories of vulnerabilities that demand immediate attention:
Buffer Overflow Vulnerabilities occur when applications attempt to store more data than allocated memory can accommodate, potentially allowing attackers to execute arbitrary code. These vulnerabilities remain particularly dangerous because they can provide complete system control to attackers who successfully exploit them.
SQL Injection Flaws enable attackers to manipulate database queries by inserting malicious code, potentially exposing entire databases or allowing unauthorized data modification. Despite being well-understood for decades, SQL injection continues to plague web applications with inadequate input validation.
Cross-Site Scripting (XSS) Vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users, potentially stealing session data or credentials. These vulnerabilities are particularly insidious because they exploit user trust in legitimate websites.
Remote Code Execution Vulnerabilities represent the most severe category, enabling attackers to execute commands on target systems without physical access. These vulnerabilities often become the primary attack vectors for ransomware deployment and advanced persistent threats.
Each category demands specific patching approaches and priority levels based on environmental exposure and potential impact.
The Critical Importance of Timely Patching
Understanding Unpatched Risk Exposure
Leaving vulnerabilities unpatched creates measurable security debt that compounds over time. Attackers actively scan for known vulnerabilities using automated tools, often exploiting unpatched systems within hours or days of vulnerability disclosure. This reality transforms patch management from routine maintenance into urgent security operations.
Recent threat intelligence indicates that most successful cyberattacks exploit vulnerabilities for which patches have been available for months or years. This pattern reveals that technical solutions exist for most security breaches—the challenge lies in organizational capability to implement patches effectively and efficiently.
Strategic Benefits of Proactive Patching
Organizations that excel at vulnerability patching realize benefits extending beyond basic security:
Enhanced Security Posture creates multiple layers of protection that make successful attacks exponentially more difficult. Each patched vulnerability represents a closed attack vector that forces threat actors to seek alternative, often more complex exploitation paths.
Operational Risk Reduction extends beyond cybersecurity to include system stability, performance optimization, and regulatory compliance. Modern patches often address multiple issues simultaneously, improving overall system reliability while closing security gaps.
Regulatory Compliance becomes more manageable when organizations maintain current patch levels. Most compliance frameworks require evidence of timely vulnerability remediation, making effective patch management essential for audit success.
Performance Improvements frequently accompany security patches, as vendors address efficiency issues alongside security flaws. Organizations with current patch levels often experience better system performance and stability than those running outdated software.
Strategic Vulnerability Identification
Modern Assessment Methodologies
Effective vulnerability identification requires sophisticated approaches that combine automated scanning with human expertise. Contemporary vulnerability assessment goes beyond simple port scanning to include configuration analysis, application testing, and environmental context evaluation.
IT Agent's approach to vulnerability identification integrates multiple data sources including vendor advisories, threat intelligence feeds, and real-world exploit observations. This comprehensive methodology provides organizations with actionable intelligence about which vulnerabilities pose genuine risks in their specific environments.
Advanced Assessment Tools and Techniques
Modern vulnerability assessment employs specialized tools designed for different aspects of security evaluation:
Vulnerability Scanners provide automated identification of known security flaws across networks, systems, and applications. These tools excel at comprehensive coverage but require expert interpretation to distinguish genuine risks from false positives.
Penetration Testing Tools simulate real-world attack scenarios to validate vulnerability scanner findings and identify complex attack paths that automated tools might miss. This human-driven approach provides context that pure automation cannot deliver.
Configuration Assessment Tools evaluate system configurations against security baselines, identifying misconfigurations that create vulnerability conditions even in fully patched systems.
Interpreting Assessment Results
Raw vulnerability scan results require expert analysis to translate technical findings into business-relevant risk assessments. Effective interpretation considers environmental factors, exploit availability, and business impact to create prioritized remediation roadmaps.
Organizations should focus on vulnerabilities with confirmed exploits in their specific environments rather than attempting to address every identified weakness simultaneously. This risk-based approach optimizes resource allocation while addressing the most dangerous threats first.
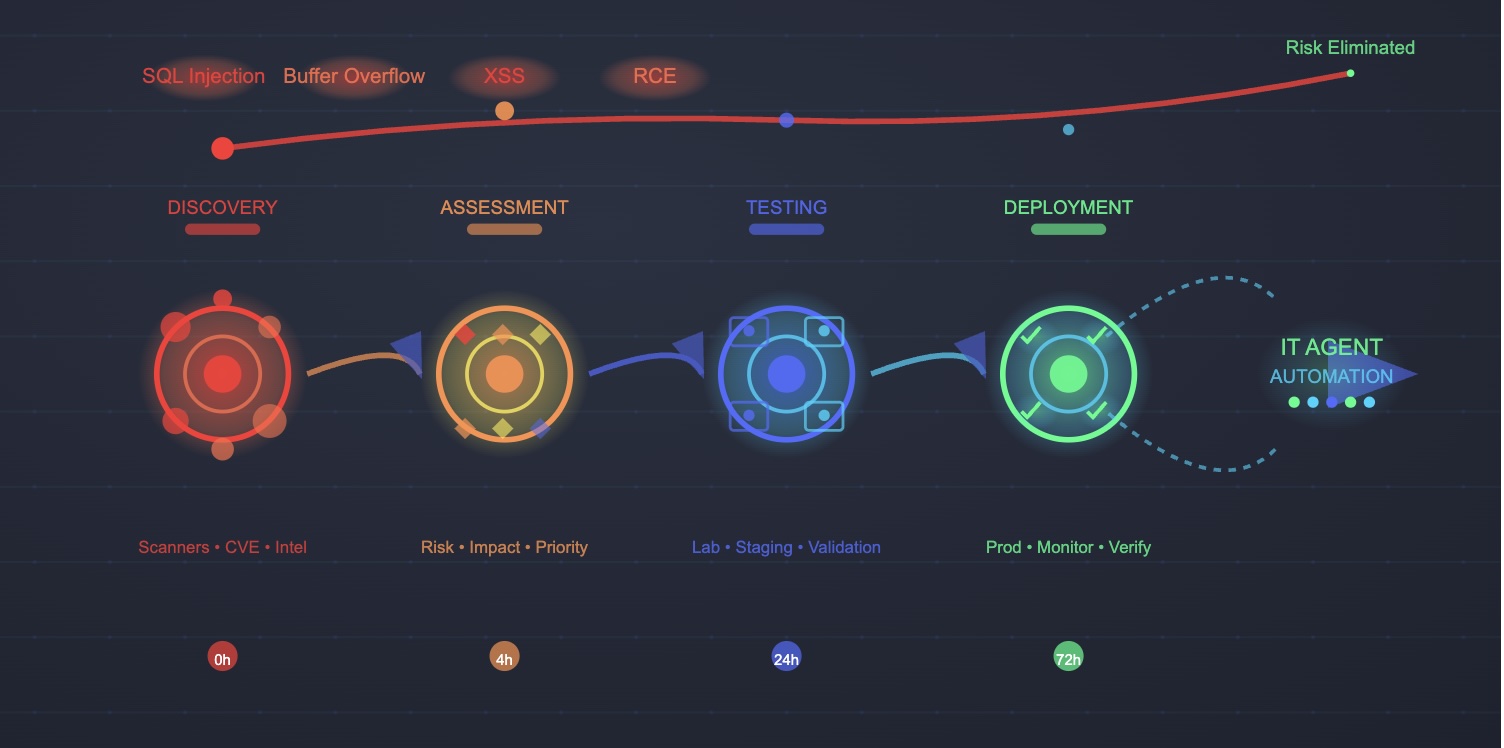
Systematic Patch Management Process
Sourcing and Authentication
Reliable patch sourcing represents the foundation of secure patch management. Organizations must establish trusted channels for obtaining patches while implementing verification procedures to ensure authenticity and integrity.
Legitimate patches should always originate from official vendor sources, security advisories, or verified distribution channels. Digital signature verification and checksum validation provide technical assurance that patches haven't been tampered with during distribution.
Pre-Deployment Testing Protocols
Comprehensive testing before production deployment prevents patch-induced disruptions while validating security effectiveness. Testing environments should mirror production systems closely enough to identify potential issues while remaining isolated enough to prevent operational impact.
Effective testing protocols include functionality verification, performance impact assessment, and compatibility evaluation with existing systems and applications. This systematic approach identifies problems before they affect production environments.
Implementation Excellence
Strategic Deployment Approaches
Successful patch implementation requires carefully orchestrated deployment strategies that balance security urgency with operational stability. Modern deployment approaches prioritize patches based on risk assessment while maintaining system availability.
Patch Management Policy Development establishes consistent procedures and accountability frameworks for vulnerability remediation. Clear policies define roles, responsibilities, timelines, and escalation procedures that ensure patches receive appropriate attention.
Risk-Based Prioritization focuses resources on vulnerabilities that pose genuine threats in specific environments. Critical vulnerabilities affecting internet-facing systems demand immediate attention, while isolated systems may follow normal maintenance schedules.
Phased Deployment Strategies minimize operational risk by implementing patches in controlled stages. This approach enables early identification of issues while maintaining the ability to halt deployment if problems emerge.
Continuous Monitoring and Verification ensures that patches achieve their intended security objectives without introducing new problems. Post-deployment monitoring validates both security effectiveness and operational stability.
Managing Implementation Challenges
Even well-planned patch deployments occasionally encounter issues requiring rapid response and mitigation. Organizations need established procedures for handling patch failures, including rollback capabilities and alternative remediation strategies.
Effective failure management includes robust backup procedures, tested rollback processes, and clear communication protocols that minimize confusion during incident response. Vendor support channels and community resources provide additional assistance when internal capabilities prove insufficient.
Building Sustainable Practices
The Continuous Improvement Imperative
Vulnerability patching represents an ongoing operational requirement rather than a periodic project. Threat landscapes evolve continuously, new vulnerabilities emerge regularly, and software environments change constantly—all requiring adaptive patch management approaches.
Organizations must establish sustainable rhythms for vulnerability assessment, patch testing, and deployment that can accommodate both routine maintenance and emergency response. This operational maturity enables proactive security management rather than reactive crisis response.
Leveraging IT Agent's Platform
IT Agent's vulnerability management platform addresses the complexities of modern patch management by providing integrated capabilities for identification, prioritization, testing, and deployment. Our approach combines automated efficiency with human expertise to deliver comprehensive vulnerability remediation.
The platform's intelligence-driven prioritization helps organizations focus on vulnerabilities that matter most in their specific environments, while automated deployment capabilities reduce the manual effort required for routine patching operations.
Measuring Success and Continuous Improvement
Key Performance Indicators
Effective patch management requires measurable outcomes that demonstrate both security improvement and operational efficiency. Key metrics include time-to-patch for critical vulnerabilities, patch success rates, and security incident reduction.
Organizations should track these metrics over time to identify improvement opportunities and validate the effectiveness of their patch management investments. Regular assessment enables continuous refinement of processes and tools.
Future-Proofing Patch Management
The cybersecurity landscape continues evolving with new technologies, threat vectors, and regulatory requirements. Organizations that invest in sophisticated patch management capabilities position themselves to adapt to these changes while maintaining security effectiveness.
Cloud infrastructure, containerized applications, and IoT devices create new patching challenges that require evolved approaches. Organizations with mature patch management practices can extend these capabilities to emerging technologies more effectively than those with ad-hoc approaches.
The Strategic Value of Excellence
Exceptional vulnerability patching provides organizations with significant competitive advantages including reduced security incidents, improved regulatory compliance, and enhanced operational stability. These benefits translate directly into business value through reduced risk exposure and operational efficiency.
Organizations that master vulnerability patching can leverage this expertise to support broader security initiatives, demonstrate due diligence to stakeholders, and build reputation as security-conscious partners. In increasingly risk-aware business environments, this reputation becomes a valuable differentiator.
The choice facing organizations isn't whether to prioritize vulnerability patching, but rather how quickly they can develop the capabilities necessary to excel in this critical security discipline. As cyber threats continue evolving and regulatory requirements become more stringent, patch management excellence will increasingly determine organizational resilience and competitive positioning.
Powerful, self-serve product and growth analytics to help you convert, engage.


